As some may be aware, our sister service, Windscribe, has been targeted by several waves of blocks imposed by Russian, Chinese, and Iranian authorities. This has impacted the quality of service for our users in Russia, China, and Iran.
It means we are doing something right - we offer a free plan to anybody wanting to escape digital censorship and extra free data allowances for people impacted by the war with Ukraine, among other things. This, apparently, upsets the authorities.
At Windscribe, we have been hard at work to get past these service blocks by using (what we like to think are) innovative solutions. When it came to this issue, the testing of our solutions required us to simulate network conditions in Russia, China, and Iran. I began by trying to use a VPN, but it quickly became apparent that there was a much better tool that would do exactly what I needed.
A wise man once said, “build something that fulfils a purpose” and “be your own customer and use what you build daily.” Taking that advice to heart, we decided to use Control D to test how it fares at simulating adverse network conditions.
Setting Up the Shenanigans
To test how our service was impacted and how our apps behaved in the face of adversity, I first needed to appear to be in Russia, China, or Iran. It was here that I first thought to myself, “Easy! I’ll just set up Windscribe at a router level via OpenVPN, connect to one of Windscribe’s Russian locations, and then connect all the devices I need to test to the router.”
It turns out that “easy” is very much an inaccurate descriptor.
Setting things up this way, I would have to::
- Factory reset my low-end router that didn’t have OpenVPN built-in.
- Unlock its bootloader.
- Flash it with custom firmware (DD-WRT).
- Set up the WAN connection (I spent an embarrassing amount of time trying to remember the credentials provided by my ISP).
- Set up an OpenVPN connection to Windscribe Russia at a router level (https://windscribe.com/guides/ddwrt), requiring me to:
- Download the OpenVPN configuration file.
- Navigate DD-WRT’s spooky interface.
- Cherry-pick details out of the configuration file downloaded and carefully select from many options DD-WRT’s OpenVPN interface offers.
- Make a few further tweaks to get it to work.
That’s a lot of steps. We’ve tried to make the tutorial as easy to follow as possible - but still, that’s a lot of steps.
I spent hours working on it before the proverbial “Eureka!” moment hit me, and I realized that I could use Control D to solve my problems in a much more straightforward way:
- Find out one’s Control D resolver from the Control D Control Panel.
- Replace the DNS resolvers set up on the router.
- Set the Default Rule in the Control D Control Panel to redirect all traffic via Russia.
That’s it. All that time was spent tweaking Windscribe when I should have spent 5 minutes with Control D. Trust me when I say I was kicking myself.
On top of that, Control D can be set up at a network level (on the router/hub/switch), at a device level (on select computers on the network), and even at an application level (browsers on the computer), which allows for a much more tailored environment - perfect for simulations.
Testing Resiliency
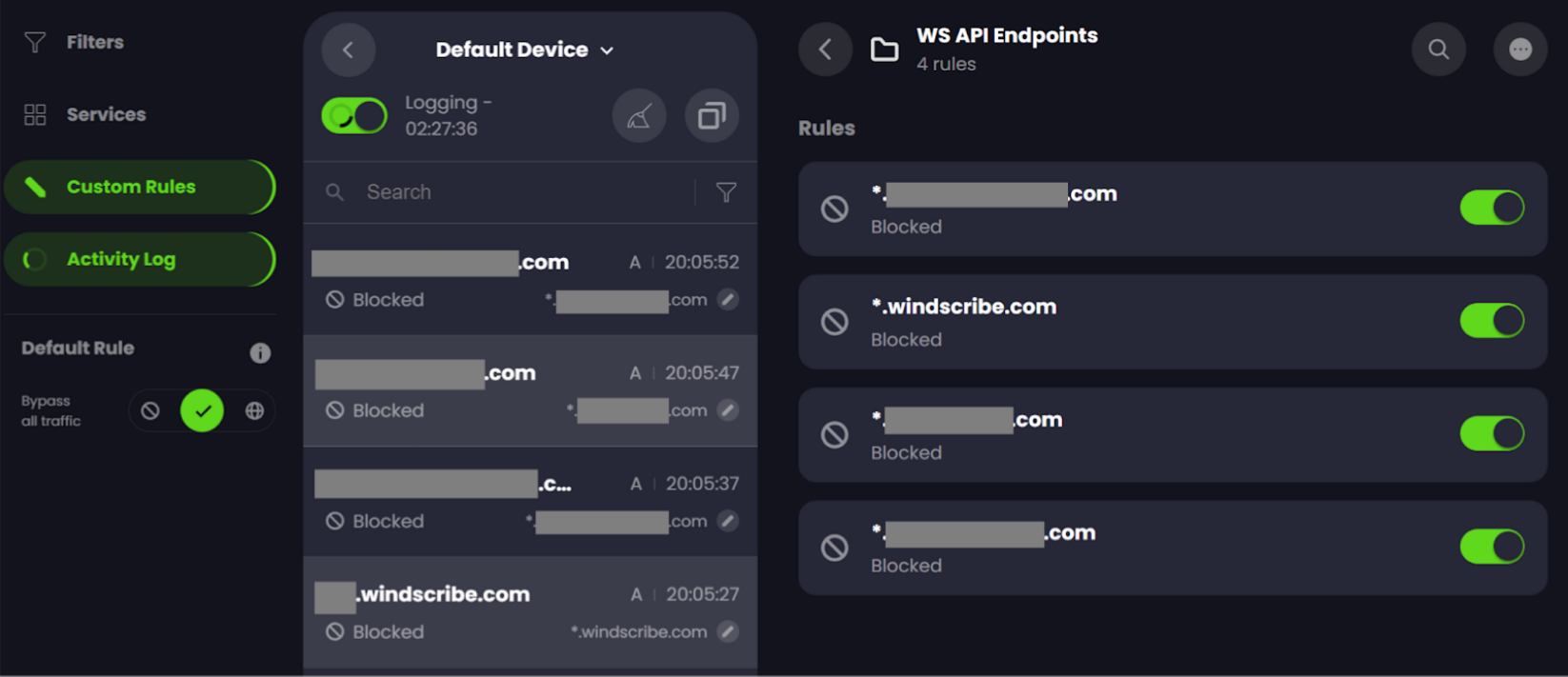
To test the reliability of our app and the resilience of our backup infrastructure, I needed to block/hijack Windscribe’s API endpoints. With a VPN-on-router setup, I’d have to block the domains using my computer's host file or create firewall rules.
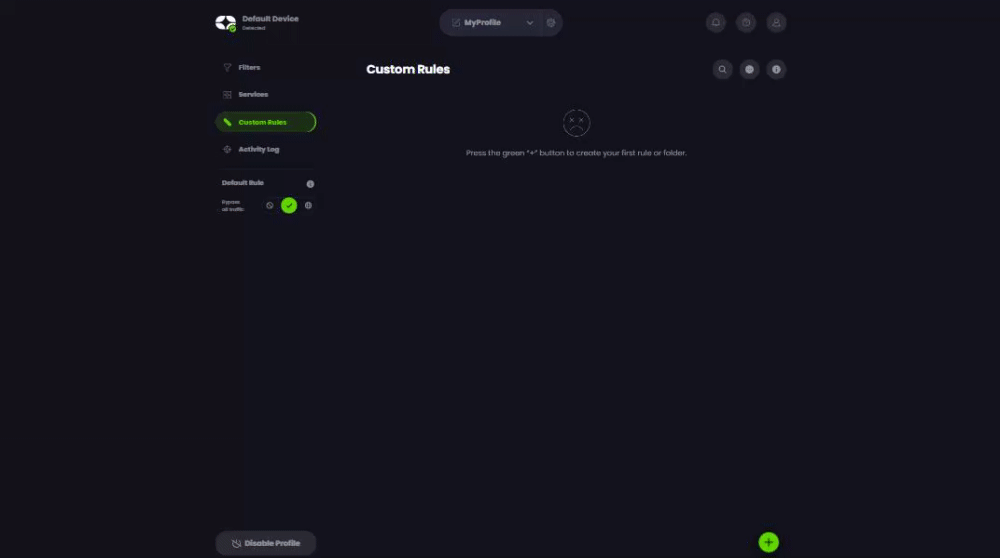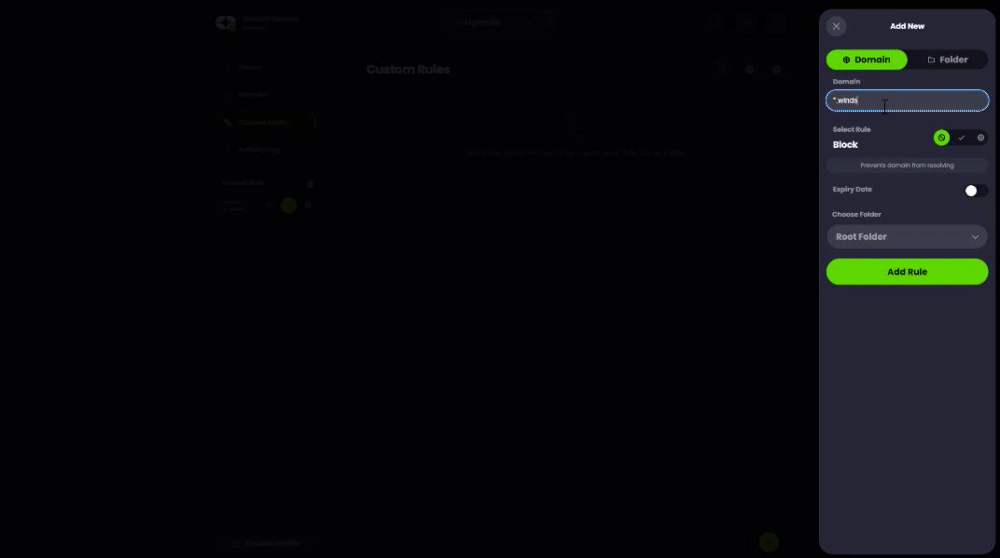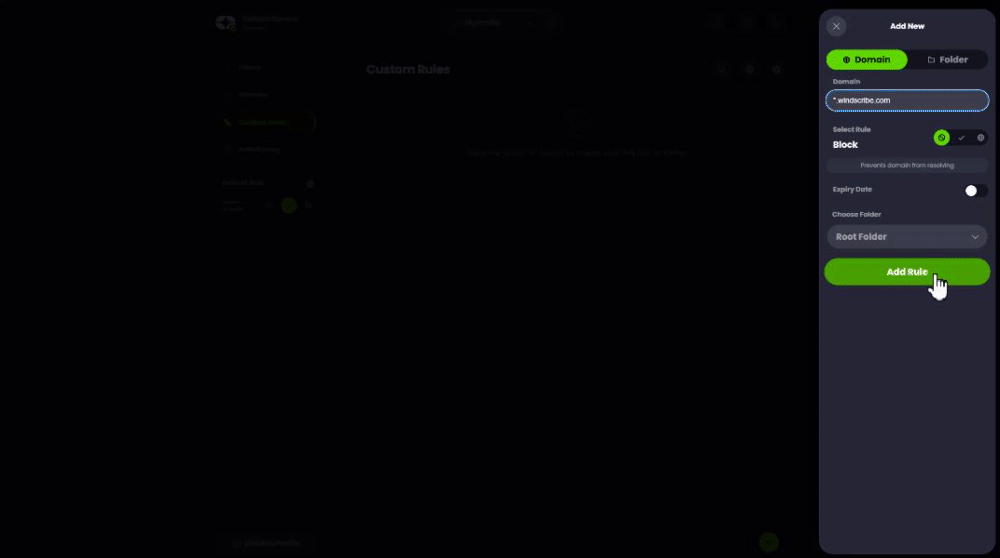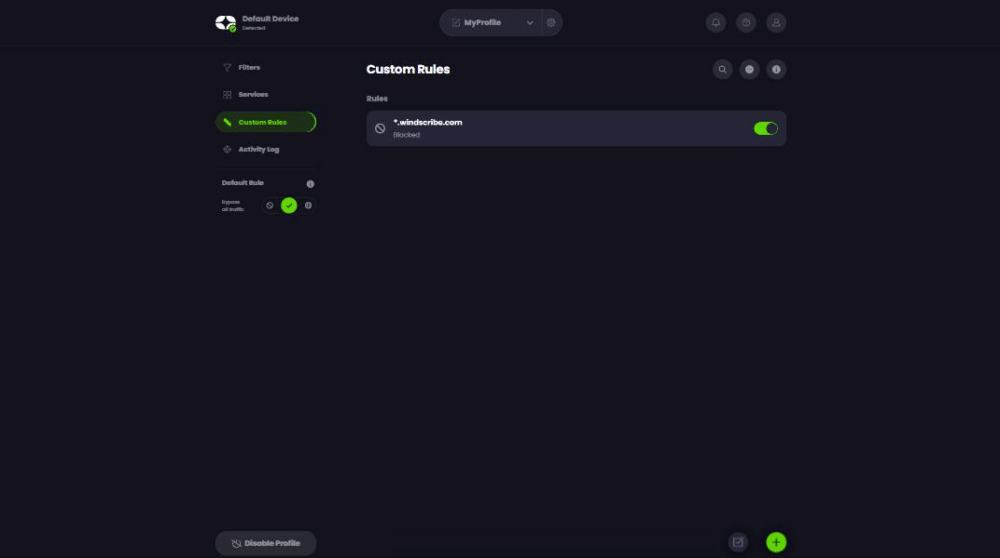
With Control D, however, it took me a few moments to create a custom rule to block (or spoof = redirect) Windscribe’s API endpoints - no fiddling on my computer or router required.
The only thing close to this is Windscribe’s R.O.B.E.R.T feature, which allows users to block/spoof hostnames. As far as we know, no other VPN service offers a similar feature.
Using the Activity Log
Not only does Control D help facilitate testing by simulating network conditions, but it also aids in analysis. In particular, the “Activity Log” feature provides insight into what is happening under the hood.
By analyzing what was working (and perhaps more importantly, what was not working), we could identify ways to get past the blocks, document the nature of the blocks, and validate that the fixes we implemented were working to our satisfaction.
Other Benefits of Using Control D
I also noted a few other unique advantages Control D afforded me. They don’t necessarily pertain to network simulations, but you’ll have to let me nerd out over them anyway!
Performance
In a VPN-on-router setup, speeds are usually bottlenecked by the router's hardware. There’s only so much a ~1 GHz processor and ~512 MB of RAM can do. However, this limitation is wholly eliminated with Control D since a VPN tunnel is not established.
For example, it’s possible that your router is capable of speeds of up to, say, 500 Mbps over WiFi. With an OpenVPN tunnel established at the router level, you could expect around 200 Mbps (if the router is high-end). If 5 devices are connected to the router, then there are only 40 Mbps for each.
With Control D, the only bottleneck is the router’s speeds over WiFi, so each device could be expected to function at 500 / 5 = 100 Mbps, provided Control D was set to redirect via a location with good hosting infrastructure. To further this point, if you are connecting your devices via Ethernet to the router, your speeds would still be bottlenecked by the router’s processor with a VPN-on-router setup; but with Control D, one would observe infinite scalability - connect as many devices as you want to the router and experience high speeds on all of them!
Molecular control
With a VPN-on-router setup, you can only connect to one location at a time, and all your traffic has to exit out of it.
With Control D, you can redirect domains and services through varying locations. This gives you a much greater degree of flexibility, letting you redirect, for example, news subscriptions like the New York Times through a US server, whilst simultaneously routing, say, Barclays Online Banking website through a server in the UK.
Further, by setting up Control D at a device level, you could control the traffic exit location, access restrictions, and even the access schedules for every single device - so your child's phone could be configured to block access to YouTube on each school night and allow access on the weekends. At the same time, their school laptop could be configured to allow access only to whitelisted educational websites during school hours and the unrestricted internet at other times.
Alternatively, your phone could be configured to route Expedia's website via Dubai, whilst your laptop could be routing Expedia's website via Frankfurt - oh, look at that, now you can compare the differential prices served by Expedia in varying regions.
Oh, the possibilities! ;)
Processing Power
Unlike a VPN, Control D uses barely any of your device’s processing power and does not require the installation of any apps. Just set it up once on your device, then control your device’s web traffic from anywhere in the world via a webpage!
Also, “reconnects” to enforce changes in the user’s preferences are a thing of the past with Control D rules since there’s no “tunnel” involved. We’re willing to wager that you’ll barely even notice it’s there (if that’s what you’re going for!).
Now Everyone’s a Hackerman
Using Control D’s granularity, performance, and analytics was a massive boon in pursuing a speedy resolution to the Russian, Chinese, and Iranian blocks; without it, I am confident it would have taken much longer to figure out what was happening.
Hopefully, this article has made you think about just how wide a range of applications a truly smart DNS like Control D has - and how you cannot wait to revel in the chance to be a real Hackerman!






